Several ways are used which hackers to hack into someone's Instagram accounts. Let us take a look at some of the most popular methods used to hack Instagram accounts to get access to them and steal valuable personal information and data.
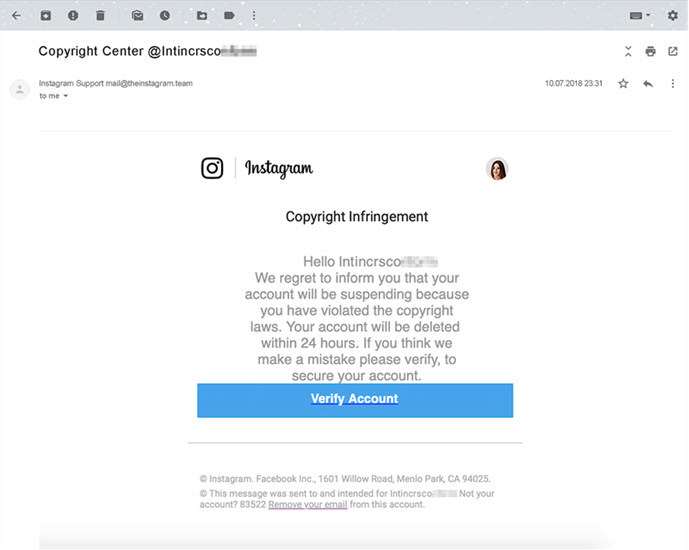
The most prevalent technique of gaining access to an Instagram account is via a phishing website.
The attacker may create a phishing page with a web host account, a free template, and some HTML understanding.
The attacker builds a bogus login page with a phishing page. The hacker gives the mark a link to the bogus login page they create, on which the victim inputs their credentials.
The phishing website logs the inputs and sends them immediately to your email inbox, giving you access to the account and the ability to reset the password.
Phishing websites are popular among hackers because they function and are inexpensive to put up.

If you know the person you're attempting to hack, try guessing their password using their personal information, such as their birth date, dog's name, parents' maiden names, or home location and telephone number.
You may be shocked at how many individuals use basic passwords, despite the warnings that this is a grave internet security error.

A zero-day vulnerability is a "software security weakness known to the program vendor but has not been patched" and may be exploited by hackers (Norton).
If a hacker discovers a zero-day vulnerability in Instagram, major security threats for Instagram users and their accounts might result. Since this uncovered vulnerability has not been officially disclosed yet, the hackers have an edge.

This is the most undervalued form of account hacking. In essence, a keylogger is a piece of software or an application for smartphones that records every word entered by the victim.
The primary issue is installing a keylogger on the target device.
You may discover both free and premium keyloggers on the internet. If you're searching for a completely free keylogger, give Smart Keylogger a try.
Finally, individuals may be hacked on Instagram by exploiting smartphone operating system problems.
These are flaws in the operating system's code or design that hackers may exploit to get access to user data.
Spylix Hacking Features And Additional Important Features
Spylix gains access to all conversations occurring inside the Instagram account being monitored and makes them accessible to you through its online dashboard. The messages include timestamps, the actual message, and the participants in the exchange.
Spylix evaluates media assets such as movies and images that have been uploaded or shared with other users over messenger when hacking an Instagram account.
After properly setup Spylix, you will monitor any activity happening on the target device in real-time. You'll get information on the target account's friends, posts, likes, comments, settings, and Instagram groups to which they belong.
Spylix, the most powerful and sophisticated hacking tool available, monitors and records messages made and received over WhatsApp, Instagram, Viber, and other social media sites.
Spylix logs every keystroke typed by the target account's user. You can see all of the passwords they enter due to this wonderful feature.
This solution provides a high level of security by prohibiting any third party from monitoring your Instagram data access. This feature instills confidence in you as a user of this product since you are not worried about your privacy.
Spylix tracks every Instagram activity in stealth mode, preserving your identity throughout the hacking process. Due to the absence of an icon on the target device, the owner of the Instagram account on which you are spying is unaware.
This hacking approach is not dependent on the device is jailbroken or rooted. As a result, the device's security is preserved.
mSpy is a well-known program that enables worried parents to monitor their children. The program is capable of monitoring both Android and iOS-based devices.
The following instructions outline how to use mSpy to discover the Instagram password for any account.
The Cocospy software is another reputable brand that may assist you in determining how to find out someone's Instagram password. The platform is capable of monitoring every activity on the target device.
The greatest part is that you would not need to root or jailbreak any device to steal another person's Instagram password.
Cocospy's other significant functions include showing the device's real-time location, viewing photographs, and monitoring social media activity.
The procedures for determining someone's Instagram password are as follows:
Additionally, you may use the Flexispy keylogger to hack into another person's Instagram account. This application is only compatible with iOS devices. This may be accomplished by following the instructions below.
To begin, you must go to Flexispy's official website.
Then register for an account.
After that, you must download the program to the target person's iPhone or iOS device.
Then, download the app and input the target person's username on your phone. You are free to snoop around at your leisure.
In today's world, it's difficult for a parent to constantly monitor their child's actions. This is when applications like Spyzie phone tracking might come in handy and aid you on time.
Additionally, the platform, accessible on both Android and iOS, allows users to join up for free.
The software enables parents to monitor their child's device's precise position. Spyzie allows users to access their texts, calls, and social media histories.
Additionally, the keylogger function will let you determine the Instagram password for the child's account.
You may refer to the guidelines below to discover how to decrypt someone's Instagram password:
You must first purchase a subscription that matches your criteria before installing Spylix on a target device.
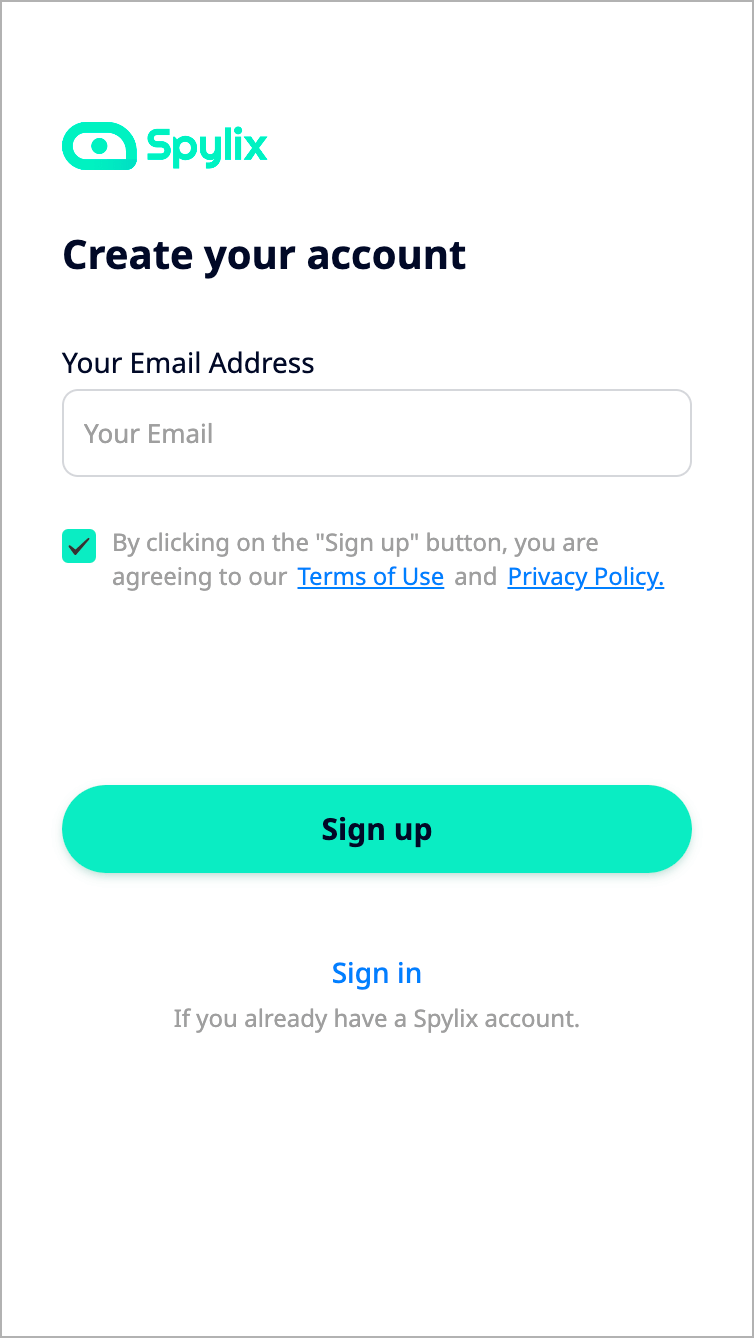
Step 1: Sign up for a Spylix account.
Create a Spylix.com account. Kindly include a valid email address since we will give you installation instructions through email. Accept the Terms & Conditions and the Privacy Statement as well.
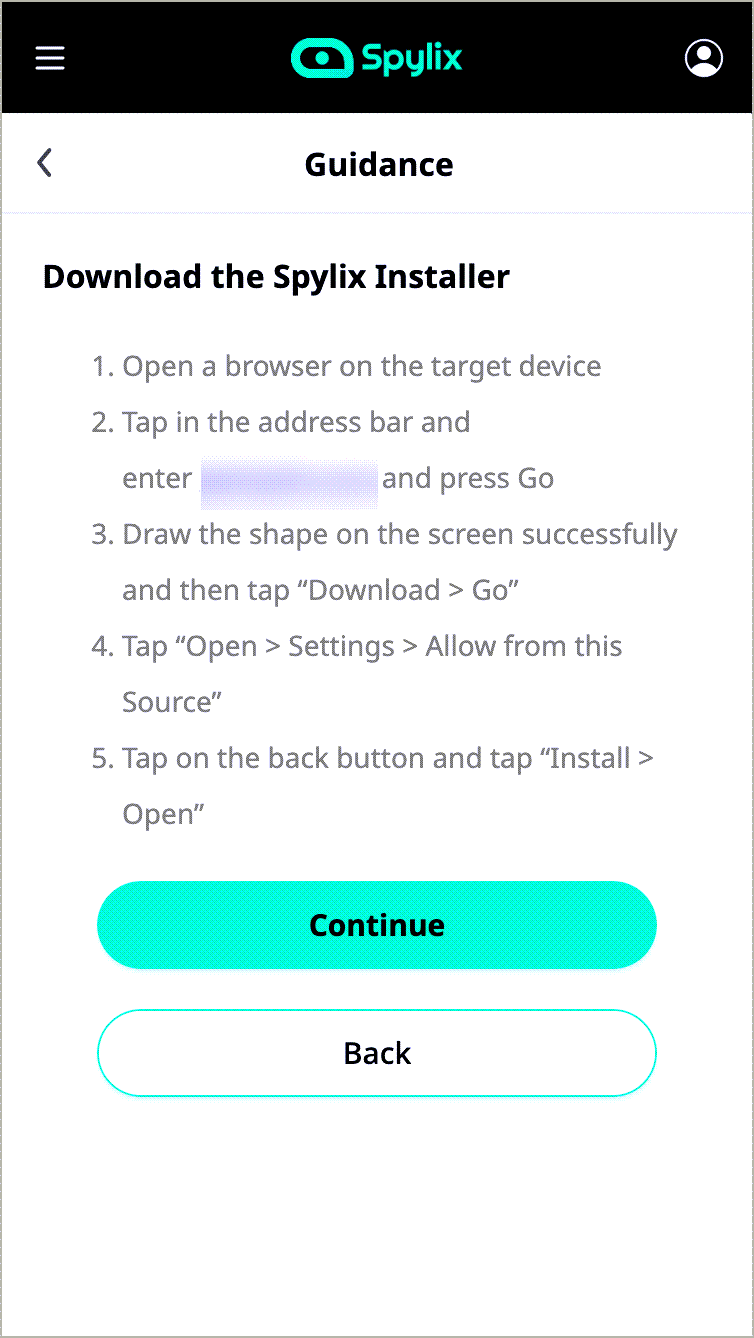
Step 2: Set-Up.
Following successful account creation, Spylix will send you an email with complete instructions on configuring your device. Continue with the tutorial until the last step.
Step 3: Disable the Play Protect feature.
You must disable Play Protect before installing Spylix on the target device. To do this, follow these steps:
Step 4: Initiate monitoring of your Instagram account
Log onto your Spylix account and navigate to the Control Panel to begin monitoring your child's Instagram online activity.
You may monitor your child's calls, websites, and social networking apps by inputting the target device's specifications (make, model, and phone number).
MyGet is another hacking tool that will capture all of your Instagram activity. As a result, you do not need the account's password to see the data. After getting it, you have access to the target's Instagram activity, among other things. You do not need to root or jailbreak your device.
MyGet needs a one-time installation and activation of stealth mode on Android. In iOS, all you have to do is validate the phone's iCloud login credentials on the main page.
Your online account will include the compromised results. The dashboard is completely cross-browser compatible. As long as you have an internet connection, you can log in from anywhere. MyGet is compatible with Android 4.0 and above and iOS 7.0 and later.
iGHack is another way for obtaining the password to an Instagram account. This does not need the installation of any program on your device. The finest characteristic of IgHack is that it cannot be tracked, which means that the other party will not be able to learn about it.
This may be accomplished by following the instructions below.
To begin, you first visit IgHack's official website. Then, click the start hack option.
After that, you must provide the target account holder's username.
The website will inquire about this. All that is required is a click on the hack button.
This will get you access to the password within minutes. Now, download the Instagram program on your mobile device.
Log in using the credentials you just discovered.
You may retrieve the password and spy around in the account using InstaRipper. This is a quick procedure that is also completely free.
The greatest thing is that this application is compatible with both Android and iOS smartphones and tablets. This may be accomplished by following the instructions below.
If you do not like to use the spyware above for Instagram account hacking, InstaPwn is one of the greatest choices accessible on the market.
This spyware, like other spyware, offers a plethora of functions. Simply install this malware on your victim's phone, and you're done.
This strategy is only effective if you have physical access to the targets' devices. So what is the point?
Both iPhone and Android users have the option of storing account passwords on their phones to avoid entering them in each time they want to check in anywhere.
If they did not use their face/touch ID to prevent access to their saved passwords, you have a chance to view them! vulnerabilities
There are various reasons why you can justify accessing another person's Instagram without their permission, but the four most typical are as follows:
While parents care about their children and desire to shield them from external risks, the absence of family time makes it easier for children, teens, and young adults to fall prey to evil individuals circulating on social media.
Another probable source of espionage is the partner when infidelity suspicions are sparked by flirting with another person.
Businesses have their methods of monitoring and controlling their staff. If one of them raises suspicions about the employee's job, it may become essential to monitor its Instagram activity.
Because many individuals use many accounts for various reasons, we may have forgotten about one of our accounts or may want to get into the account of someone who has died away to remove all Instagram activity.
The most effective technique of securing your account is to design a strong password that includes both upper and lower case characters and numbers.
You may enable two-factor authentication in your Instagram settings to safeguard your account. You'll be prompted to choose either text message codes or a third-party authentication app as the main security option when you enable it.
Avoid including private information in your images, descriptions, or other public areas. Never share your password with someone you do not know or trust.
Surveillance applications are available on the market that enables users to follow a device remotely, so avoid lending your phone to strangers or installing unfamiliar programs on your device.
Make a habit of checking your phone regularly to see if any unfamiliar apps have been installed and, if so, remove them.
You've now discovered the most effective methods to hack an Instagram account. If you want to hack without gaining physical access to the target device, a phone Spylix program may be a viable option.
Spylix's all-in-one monitoring capabilities may also be fairly simple for first-time users. Why not download it and give it a go at hacking children's Instagram accounts and implementing parental controls?
There is so much you can do with Spylix that there’s simply no way to fit them all into one short list. Here are some of the prominent features that our customers love the most!