Hacking has changed a lot since its starting days. As more tools are becoming readily available, you can even hack an iPhone in a matter of minutes.
Today in this article, we will take you through the various methods available to complete the hacking process, answering how to hack into iPhone remotely.

Generally, hacking is considered malicious and evil. However, it becomes necessary when it comes to the safety of your loved ones or to verify something suspicious.
If you feel a slight change in your spouse or partner’s behavior, and suspect that they are being unfaithful, then hacking their iPhone is the only option to verify it.
Surely, such activity is certainly better than confronting them face to face, which could damage the relationship, especially if your mistrust is wrong.
Also, parents can employ such tactics on their children’s phones so that they can know what their child has been up to, or what places they are visiting.
And, it allows the parent to act immediately in case their child is in danger.
So, the question now is how to hack someone’s iPhone?
Well, check out the next section for a complete tutorial!
The simplest and easiest way to learn how to hack an iPhone remotely free of cost is by simply using the help of a third-party app such as Spylix.
This app abstracts the complete hacking process from you and provides almost full access to another device’s data.
Besides, it is geared towards parents who want to keep their children safe yet don’t want to impose strict restrictions.
Additionally, Spylix is also not platform-dependent and will work on both iPhones and Androids without the need for invasive methods such as jailbreaking or rooting the device.
Understand how to hack an iPhone without a password using Spylix here:
Step 1: Create your user account with a valid email address.
Now, select iPhone as the target you want to target. Next, pick any pricing plan!
Step 2: Add Spylix
There is absolutely no requirement to add the Spylix app on the other user’s iPhone.
Just, enter their iCloud account to complete the verification process, and that’s it!
Step 3: Remote Hacking iPhone
Finally, from your Spylix account, click Start Monitoring to open the Online Dashboard.
There, you can access all the features offered by the service to hack iPhone.
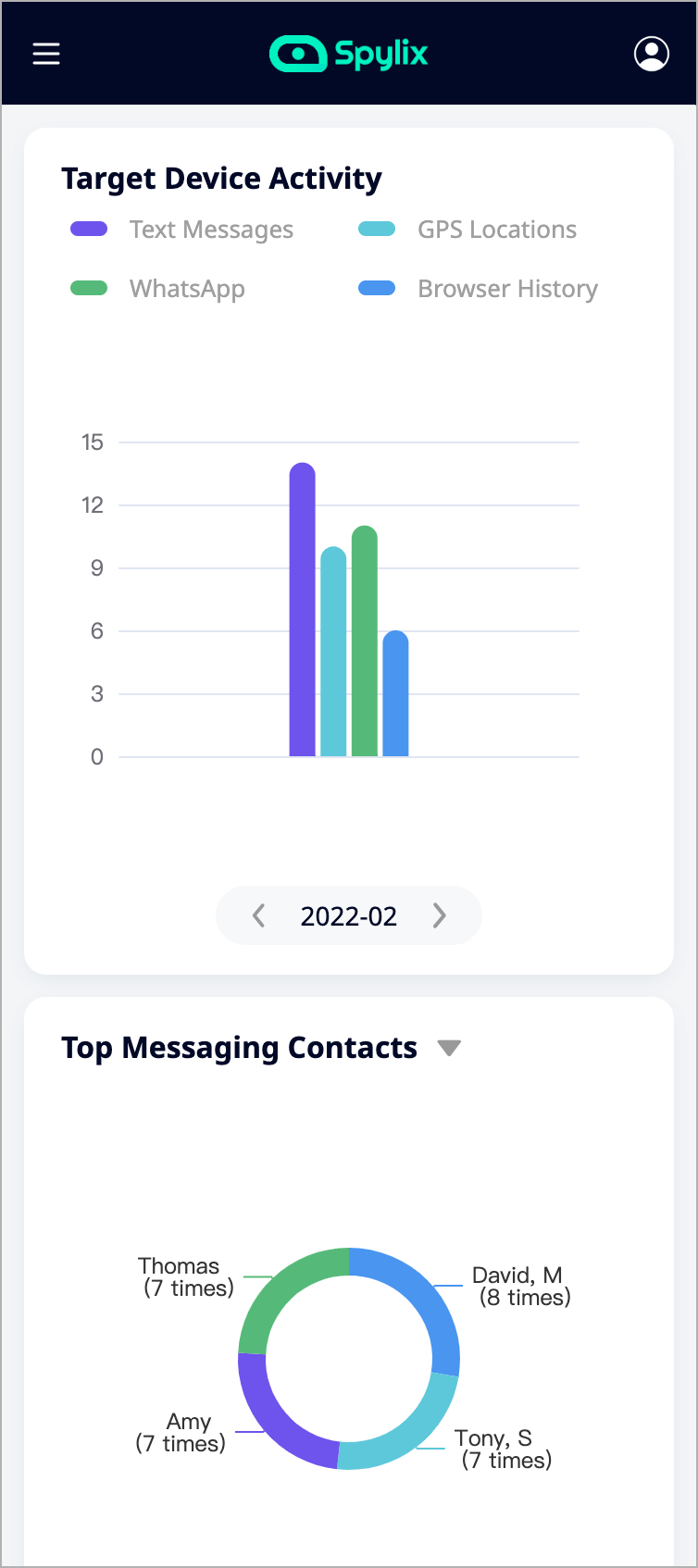
If you are wondering what Spylix brings to the table, then read through this section as we will highlight several advantages offered by this application.
Dedicated Stealth Mode
Spylix has a built-in stealth mode that attempts to completely wipe off the app’s trace from the target device. This stealth mode ensures that the person using the target device never finds out that they are being spied upon, leading to serious troubles.
Easy Access to Data Through an Online Portal
Spylix also has an online portal where it allows you, as the user, to see details about the target device. All the features and settings of the app will be controlled from there.
See how convenient it is learning hack into an iPhone!
Although we highly recommend a third-party app to ease the process for you, if you are looking for other alternatives, here are some free solutions to learn how to hack an iPhone without having access to it.
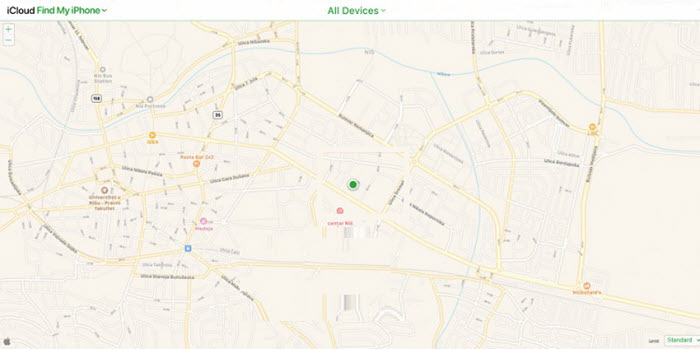
You can use one of the built-in utilities available across all iOS devices like Find My iPhone to find out the present location.
Also, this feature comes in handy when locating lost Apple Watch, Mac, AirPods, and iPad.
Have trouble using this feature? Read the following guide:
Step 1: Access iCloud.com/find using your web browser. There, enter the user (whose iPhone you want to hack) iCloud account info.
Step 2: Once signed in, click All Devices and view the current position of the iOS device on the map.
There are no direct free methods that facilitate hacking an iPhone through an Android.
However, if the target user does use Google Drive and you have access to their Google Account details, then it is probable.
For it, you have to sign in using their account info on your Android and reach the required information.
An iPhone can also be hacked through a computer.
Yet, you will need the target device’s iCloud details. Navigate to iCloud.com and enter the details if you have the required information.
All the data stored in iCloud by the target user will be displayed right on your computer.
From here, you can download any specific file you want, and when you are done, simply log off from the iCloud website.
One of the most widely popular methods to learn how to hack someone’s iPhone is using the WiFi connection. The most common and quick method is a man-in-the-middle attack.
Its working and dynamics are quite complicated for a beginner, starting with a hacker sending an official email or text message asking the target user to log in to their account or confirm some data by going on the link mentioned.
Once they click the link, it will direct them to the scam website, making it possible for you to access the iPhone’s contents.

The internet is filled with the buzz that iPhones can be hacked by tricking Siri as newer operating systems have enhanced security and safety options, especially when it comes to the built-in features of Siri.
So, it’ll be much easier for hackers if one has an outdated phone, especially with iOS 10.3.
All you have to do is ask Siri some minimal questions like a calculator or what time it is that can cause it to open any built-in app on which you can type.
After that, you can tap the plus button to switch to a messages app through which you can creep into the Home to unlock the target iPhone.
It is quite easy to hack any iPhone using a passcode as all you need is a keylogger utility. This utility can store all the strokes made in any device.
Sure, you’ll find this in various applications around the internet that can be anonymously installed on any iPhone.

This way, whenever the passcode is being typed, it can be stored or recorded that you can later see using the app. In such a similar way, all your login credentials can be accessed.
Additionally, Spylix offers the Keylogger feature to perform this method conveniently.
There are numerous ways through which someone can hack your iPhone without even accessing it.
So, it gets pretty tricky to figure out whether someone is currently accessing it or not.
Initially, you can implement some basic ways of finding out, like checking the devices that are signed in using your Apple ID.
All you need to do is go to the Settings following the panel with your name. This will automatically lead you to the list of devices currently using your Apple ID.
Hence, if you can locate any unknown device from there, tap on that and remove it.
You can also check if the device has recognized any other fingerprint or face ID for unlocking to avoid any unknown person going through your phone when you’re away.
Just sign in to your Apple ID and scan all the personal information and security options within your account to find if any external information has been added.
However, if you wish to learn how to hack an iPhone remotely free of charge and without getting detected, try Spylix.
The target will be clueless as you can view their real-time location, social media chat history, call logs, and more!
There was a very dangerous vulnerability on the iPhone, discovered by Google’s security researcher Sean Wright.
The researcher found out that this vulnerability requires zero interaction from the target user to exploit, unlike most common exploits that either require physical access to the device or some action performed by the target user.
The exploit then allowed almost complete access to the device along with the camera and microphone functionality.
In the words of Sean Wright:
“Typically, they require some user interaction, such as installing a malicious application. It appears that this vulnerability only requires the attacker to know the user’s phone number to be able to exploit it.”
Still, there is no need for you to worry as this issue has been fixed by Apple.
Nevertheless, to make sure you are protected by this problem and to protect your data from leakage, be sure to keep your device updated.
Of course, there are reasons why one may choose not to update. Still, this vulnerability is a severe threat to iPhone users, so the phone should be updated.
Besides, if you want to control your data flow further and keep everything secure, make sure to head into settings and limit the apps responsible for it.
So, you now know several methods that can be used to hack into someone’s iPhone. However, not all approaches have the same effectiveness.
Spylix makes understanding how to hack into iPhone simpler and easier to follow.
So if that’s something you are aiming for, choose Spylix and save yourself from all the complications.
There is so much you can do with Spylix that there’s simply no way to fit them all into one short list. Here are some of the prominent features that our customers love the most!