The internet has brought both good and evil and ways to deal with the wicked. As much as we love the idea of smartphones connecting us to the internet, there is more data within the hacker's grasp.
That is why you will hear of constant contact hacks as tech companies devise ways to keep the information secure. This article explains more about contact hacking and how it happens.
So, you will know about its existence and how to do it in addition to prevention measures in case you get hacked.

A contact hack is simply a way that attackers use to get what's saved in your contacts application or phone book. These days, we save more than just the numbers. You have the name of the phone number owner, the number itself, and other supporting information.
Therefore, a contact hack in the current era will mean a lot of picking up the phone to the saved work email. Our phone numbers are also attached to many applications such as emails, social media apps, and two-step verification processes from various applications.
So, that means the contact hacker can use your number to get more information from other contacts from other applications. If you had never thought about it that way, it's time to recognize that contact hacking is bigger today than 15 years ago.
Now, here comes another question, can your phone contacts be hacked?

If you are still asking the question above, the answer is yes, but how do the attackers go about it? People have been searching for how to hack contact numbers from another mobile for a long time.
There are various solutions for that, and they range from applications to contacting IT technicians with superficial skills. So, it's something doable. You may have heard of scammers sending you malicious emails to subscribe to services or buy products.
Once they get hold of your email, they can find a way to get all the other emails together with the contacts synced to the cloud from your phone. In other cases, you may get links sent to you via email or social and messaging applications.
Clicking the link may lead you elsewhere, but they could be aiming at your contact list and other information for the attackers. In some extreme cases, you may get messages that your phone is under attack, and you should take the necessary steps to enhance security.
Those with iPhones are fond of this from their calendar. Once you obey the notification, you see scam notifications as the attackers enjoy the gateway to your phone contacts and anything else saved on the phone.
Lastly, the app's method is where an installation happens before accessing information remotely. These apps mirror what is on your phone and display it in the same way on a remote dashboard.
If you want to view someone's contacts on the dashboard, all you need is to click on the ‘Contacts' tab or something similar. Let's see how one of the best apps works when you want to hack someone's contacts without their knowledge.
Spylix is a phone-hacking solution with many capabilities. It performs a quick contact hack and gets you more information from a targeted phone. It displays the details remotely and what you get in your online account is a dashboard with all the phone features.
For you to hack contacts from another phone, Spylix requires a one-time setup. You can use it on Android or iOS phones without rooting or jailbreaking. It's an app with cutting-edge technologies, so there is no need for such techniques.
Androids require a one-time installation. The setup happens online on iPhones since the application works with iCloud to remotely avail the information. As you view the results in your online account, Spylix will be working quietly in the background.
On the dashboard, you will view the whole contact list as it appears on the phone. The names will be there together with the phone numbers. If there is any additional information, Spylix will not skip that.
If new numbers are not on the contact list but are already dialed on the phone, they will be under the call log feature. You can also use the keylogger to see the keyboard records.
There are apps used to identify unknown numbers. With Spylix, you can check on the third-party installed applications since there is a specification for that. If you find something like Truecaller, among other apps, you can check to see the name of the unknown callers from the phone.
It seems like Spylix can achieve a lot when hacking contacts. It also has the social networks tab to get more contacts from those in the social media accounts and apps like WhatsApp.
The online dashboard helps in remote viewing via your account, and it works with all browsers. That permits you to view the contacts at any time if you are connected to the internet.
Step 1: Register an account with Spylix and select the targeted phone's operating system. Subscribe to one of the plans and then check the instructions page for more directions.
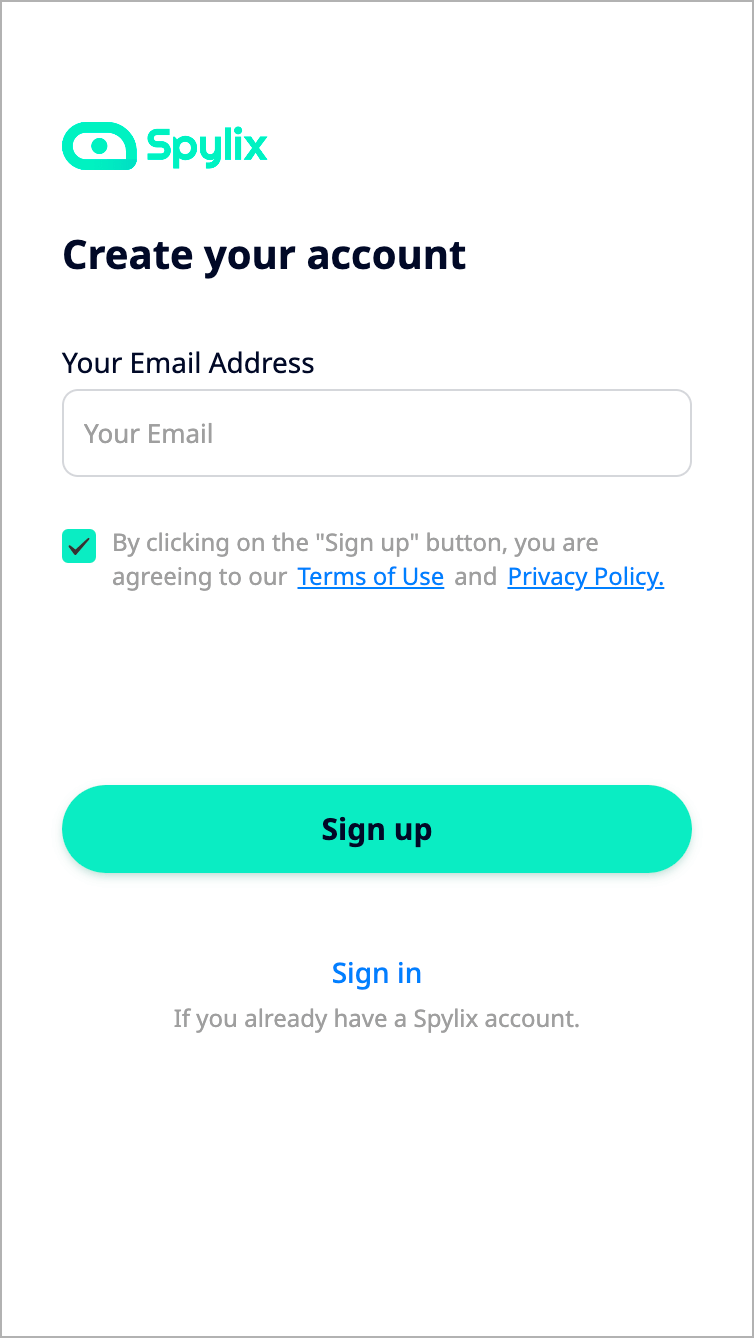
Step 2: In Android, use the link presented to install the app once on the phone you want to hack.
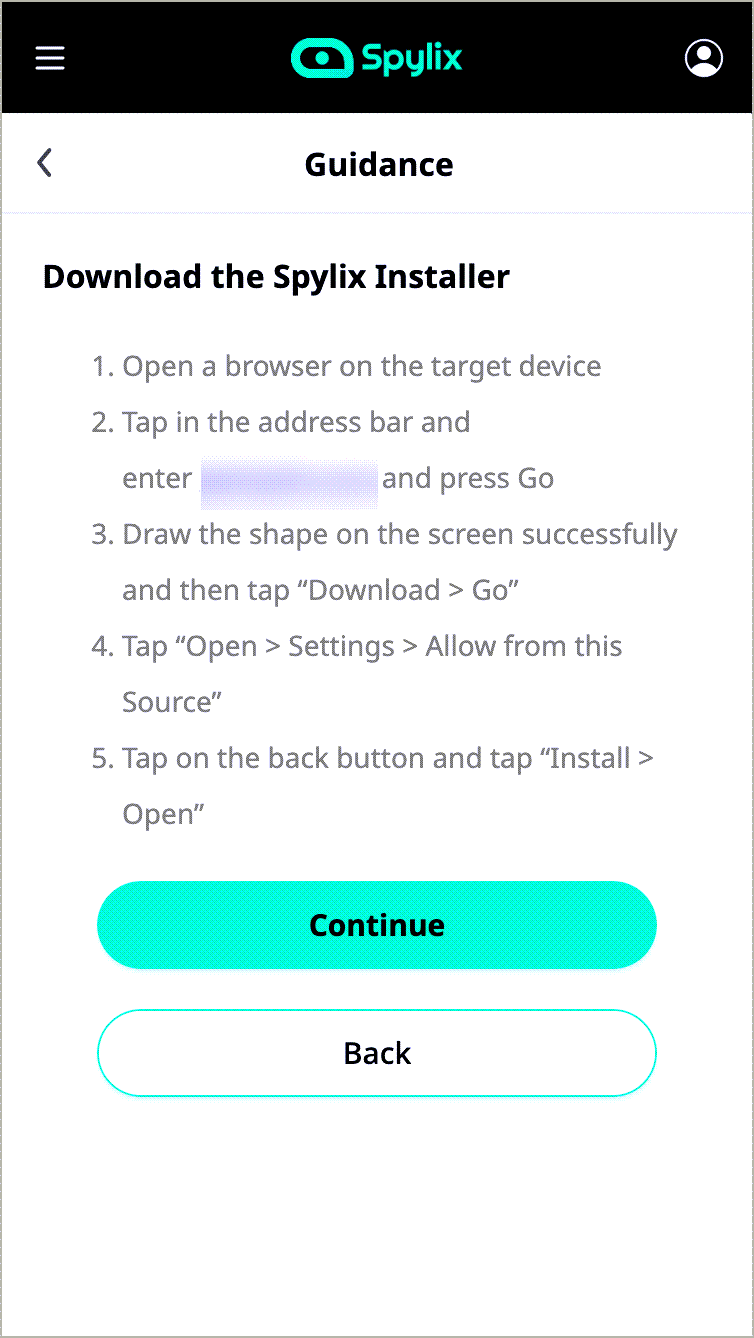
In iOS, use the iCloud ID to verify online.
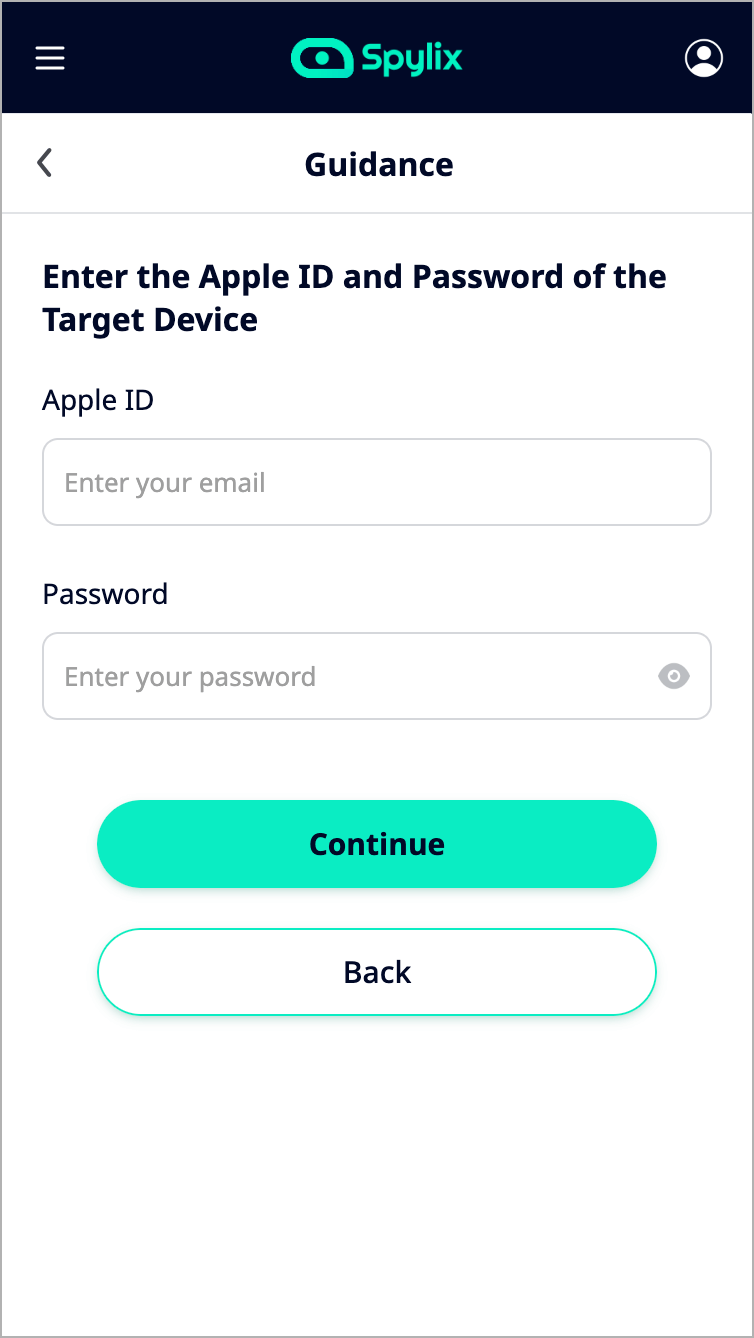
Step 3: Log into your account using another device and access the dashboard. Click on the contacts tab to view all the saved details. Use the call log to check for more information. Anything else you require to access is indicated on the left menu.
If you have experienced a contact removal hack or someone can access them, there is a need for swift measures. You can use various approaches to bring back the peace and block future illegal access to your phone.
The first move is to check on any suspicious apps you haven't downloaded before. Go to your settings and check on manage apps or where you can view and uninstall applications.
If there is any app in the list that you don't recognize, get rid of it by tapping on the uninstall button or icon. The next part is installing an antivirus or ensuring that your phone security app is up to date.

If you think the inbuilt security protocols are not helping, you can install a trustworthy antivirus from the application stores. Scan the phone after uninstalling all the suspicious applications to remove anything left that is malicious.
If there are no improvements, you can try the last step, factory resetting. This move restores your phone to how it was when new. Ensure that you have backed up all the information before using this move.
For prevention measures, you can avoid installing apps that ask for too much information from you. Also, avoid clicking unknown links or surfing using public Wi-Fi.
Start by removing all the malicious applications on your phone. Go to the settings in your phone, access the apps manager, and remove any new apps you are not aware of or have never installed.
Scan your phone using the latest antivirus updates and install an antivirus if needed. The last move can be to back up your contacts and factory reset your phone.
You can use an application such as Spylix to view contacts from another phone. Just install the app on the Android once or use the iCloud ID to verify online for the iPhones. After that, use your online account to view the contact list and the call log.
If someone has hacked into your email, they can view the synced contact list from your phone. Other ways to hack the contact list include clicking unknown links that install unknown apps that fetch the contacts and other information from your phone.
If you also receive fake alerts on your phone, responding to them may lead to contact hacking, among other malicious activities.
People have been complaining about constant contact hacks or seeking ways to do it. We hope that the information above will help you protect your device and fetch contacts from another phone when needed.
Ensure that your security is up-to-date and do not click or venture into the unknown, especially if it has a connection to the internet. For those who require an application to hack contacts and other details, Spylix is the globally recognized tool to help you do it.
There is so much you can do with Spylix that there’s simply no way to fit them all into one short list. Here are some of the prominent features that our customers love the most!